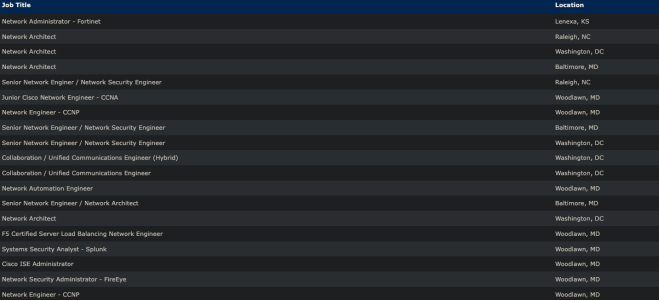
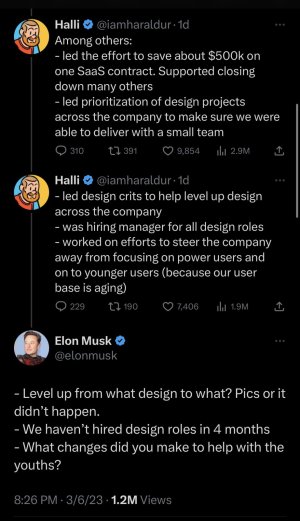
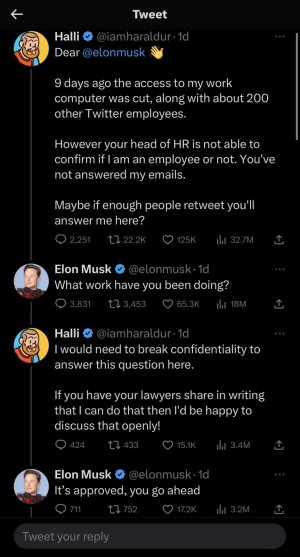
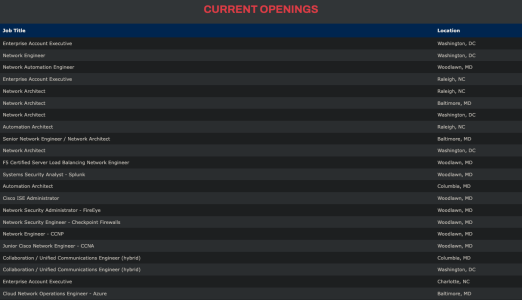
Belgium
formerly colombia
- 26,006
- 37,280
- Joined
- Jan 12, 2013
Passed the entry exam so I'll be starting my programming education (specializing in .NET) soon, unfortunately I'm on a waiting list for probably a few more months.
Normally I was supposed to become a nurse but had to drop out somewhere in the final third of my first year due to an emergency partial lung removal surgery and subsequent chronic illness that made the physical aspect of the job impossible.
I was poor at the time and had a big (by Belgian standards, €4400) medical bill from the surgery so a US friend helped me get back on my feet financially by teaching me a bunch of stuff about the market for certain social media usernames and finding and exploiting security vulnerabilities in websites. The two go hand in hand.
IT initially didn't really interest me much before my illness made it clear I had to look for a different career but that time hunting and exploiting vulnerabilities was some of the most fun I've had.
Normally I was supposed to become a nurse but had to drop out somewhere in the final third of my first year due to an emergency partial lung removal surgery and subsequent chronic illness that made the physical aspect of the job impossible.
I was poor at the time and had a big (by Belgian standards, €4400) medical bill from the surgery so a US friend helped me get back on my feet financially by teaching me a bunch of stuff about the market for certain social media usernames and finding and exploiting security vulnerabilities in websites. The two go hand in hand.
IT initially didn't really interest me much before my illness made it clear I had to look for a different career but that time hunting and exploiting vulnerabilities was some of the most fun I've had.